It's January 2025, so it's a perfect time to reflect on everything in 2024. In this article, we explore what the PVS-Studio team introduced last year: new plugins, integrations, features, and much more!

PVS-Studio is a static analyzer that detects errors and potential vulnerabilities in C, C++, C#, and Java code. The tool is used to monitor and enhance code quality.
For more info, please consult the product page.
Java project analysis in Visual Studio Code
In 2023, we introduced the PVS-Studio plugin for Visual Studio Code. It has come quite a long way from a simple report viewer to a full-fledged feature for analyzing C++ and C# projects. And the journey is far from over!
In 2024, our team added the analysis of Java projects in the PVS-Studio plugin for Visual Studio Code! Now the Java plugin enables developers to:
Enhanced mode to mark false positives and other fixes for Visual Studio
The PVS-Studio plugin for Visual Studio 2024 now includes a new mode that considers the source code line hashes with issued warnings when users mark warnings as false positives.
Prior to this, hashes were used for navigation and operation of suppress files. The new mode allows developers to track whether the line has changed since its warning was marked as false positives. If the line has been changed, the marker of a false positive will no longer suppress the warning.
std::string(4, std::string().at(0)); //-V530 //-VH"920700501"Note. To learn more about enhanced mode to mark false positives, refer to the documentation section.
In version 7.33, we've fixed compatibility issues between the PVS-Studio plugin and Visual Studio 2022 (versions 17.12 and later). We can't help but share—a user has pointed out this error! Our support team is standing by to help with any issues you encounter. So, don't hesitate to let us know if something breaks or if you have any ideas on how to enhance the analyzer!
New requirements for IntelliJ IDEA, CLion, and Rider
To maintain plugin stability and compatibility in 2024, the minimum supported versions of JetBrains IDEs for our plugins have been raised to version 2022.2.
Additionally, our team has added support for .pvsconfig files to configure diagnostic rules in the PVS-Studio plugin for CLion.
Note. To learn more about .pvsconfig files, refer to the documentation.
Qt Creator plugin enhancements
The PVS-Studio plugin for Qt Creator—like the plugin for Visual Studio Code—was introduced two years ago, in 2023. In 2024, we vastly expanded the range of supported IDE versions:
Along with supporting new versions, we've also started retiring deprecated ones. The first to be retired was Qt Creator 8.x, released in July 2022. We've decided to support all official Qt Creator versions no older than two years.
Note. To learn more about the PVS-Studio plugin for Qt Creator, refer to the documentation.
Splitting the SonarQube plugin
In 2024, the PVS-Studio plugin for SonarQube was split into two separate ones.
It was all about the modified SonarQube API: the severity level of warnings was incorrectly displayed in the list. To resolve this, we had to split the plugin into two. You can read about these changes in our article.
Note. To learn more about how to use the PVS-Studio plugin for SonarQube, refer to the documentation section.
New integration: CodeChecker
In 2024, many users requested it, and we couldn't help but deliver it! We implemented the PVS-Studio reports in CodeChecker, the server which provides web interface for viewing and aggregating static analysis results.
Note. To learn more about PVS-Studio in CodeChecker, refer to the documentation section.
New functionality for Unreal Engine
Last year, we added support for SN-DBS, the distributed build system, to ensure better integration PVS-Studio with Unreal Engine (starting with Unreal Engine 5.5.)
Note. To learn more about the PVS-Studio integration into SN-DBS, refer to the documentation section.
We've also made numerous other improvements to the PVS-Studio for Unreal Engine. If you're interested, we invite you to read the article, which describes them in detail.
Documentation revision
Throughout the year, we continued enhancing our documentation. We added new documentation sections for the latest features and diagnostic rules, while also revising the existing ones.
For example, we updated the documentation for integrating the analyzer into CircleCI, the cloud CI system. In the section on analyzing C and C++ projects with the JSON Compilation Database, we've added instructions for working with the Bazel and SCons build systems.
Modified file analysis mode
A new modified file analysis mode evaluates file hashes and saves them to a dependency cache. At the next run, only files with changed hashes will be analyzed.
Currently, you can analyze modified files in MSBuild C, C++, and C# projects on Windows using the PVS-Studio_Cmd utility and in C# projects on Linux/macOS using the pvs-studio-dotnet utility.
Note. To learn more about the modified file analysis, please refer to the documentation.
PVS-Studio is now on ARM!
PVS-Studio has been available on macOS since 2019—but until now, it only supported x86 processors.
That changed with version 7.34! The latest 2024 release has brought full support of PVS-Studio on macOS for processors with ARM architecture.
Note. Download PVS-Studio on the page. To learn more about how to install the program, refer to the documentation.
The enhanced individual file analysis mode
In 2024, we extended the individual file analysis in the pvs-studio-analyzer utility, introducing the ‑‑source-files flag. This made it possible to streamline the utility usage when the compilation dependency cache for C and C++ files differs from the project structure.
Note. To learn more about the cache of compilation dependencies for C and C++, refer to the documentation section.
GNU RISC-V GCC Toolchain support
We supported the GNU RISC-V GCC Toolchain on the RISC-V platform for C and C++ analyzers.
Memory optimization for template instantiation analysis
We made significant strides in reducing memory usage when analyzing template instantiations in C++. Thanks to our team's efforts, the average resource consumption of the analyzer was significantly reduced. One of the open-source projects we used for testing showed a reduction in memory usage of over 90%.
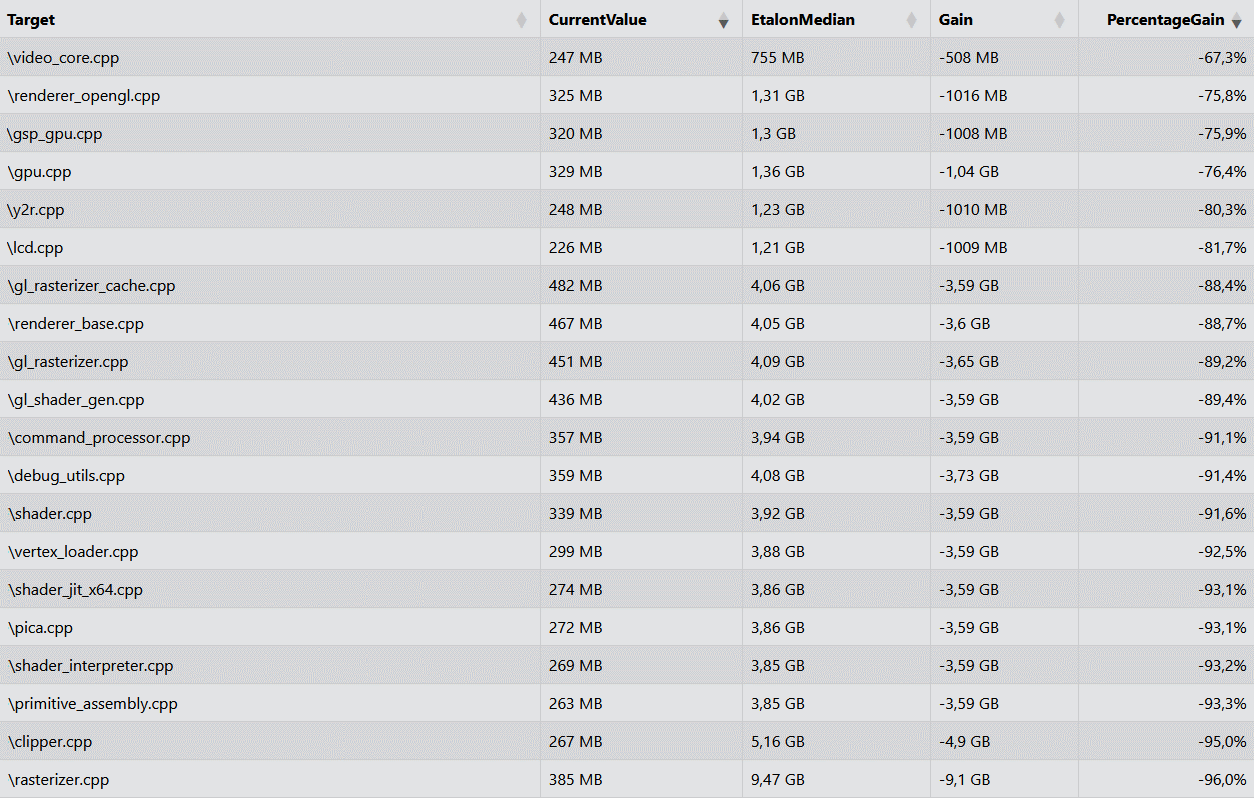
Try the updated PVS-Studio analyzer here!
User annotations
PVS-Studio had various mechanisms that helped tailor the analyzer for the specific code base and enabled users to customize diagnostic rules.
Note. To learn more about the additional configuration of the C and C++ analyzer diagnostic rules, refer to the documentation section.
However, in 2024, we took it a step further and implemented a more powerful mechanism: user annotations in JSON files. This new format offers greater flexibility, scalability, and readability compared to the previous functionality. It also allows users to annotate even third-party code by marking user-defined functions and types. Even now, the new user annotation system enables developers to set the following parameters:
std::unique_ptr, std::string, std::vector, etc.;noreturn), declared as deprecated, etc.;nullable object should be valid, the parameter should differ from other parameters, etc.;nullable object is always valid, etc.How user annotations help the analyzer? You can find the answer in the article: User annotations for PVS-Studio.
Note. To learn more about user annotations, refer to the documentation section.
The enhancement: analyzer parsing
In 2024, we made significant improvements to C++ code parsing.
Enhancements:
New features:
boost::unique_ptr and boost::shared_ptr;Diagnostic rules (General Analysis)
Requested by users
MISRA
During the year, we've published 45 articles dedicated to the C++ language. As it turned out, the most popular ones are about arrays:
Throughout the year, we've been working on an especially gorgeous project that's quickly gaining popularity. Now we're thrilled to present the full version of the e-book dedicated to undefined behavior in C++. Written in collaboration with Dmitry Sviridkin, an experienced software engineer, and Andrey Karpov, co-founder of PVS-Studio, this guide will be a trove of knowledge for developers.
C++ programmer's guide to undefined behavior consists of 12 parts that explore the most mysterious and exotic aspects of undefined behavior. The authors share practical examples and tips to avoid common development mistakes. This book will not only be useful but also entertaining for anyone working with C++.
New .NET version support
In 2024, the C# analyzer team supported the analysis of projects under .NET 9, including all its latest features.
Note. If you're curious about what's new in .NET 9, you can check out our overview article.
PVS-Studio quickly adapts to new versions of .NET and C# after their releases. To ensure you don't miss a new analyzer version, subscribe to our release digest.
User annotations for the C# analyzer
Like in C++, we added user annotations in JSON format to the C# analyzer.
These annotations allow developers to mark types and functions to provide the analyzer with additional data, enabling it to detect more bugs. Such annotations should be in a special file of JSON format.
At the moment, user annotations in the C# analyzer are available only for taint analysis.
Now, users can mark sources and sinks of sensitive data, which helps the analyzer more precisely identify potential vulnerabilities in a given project.
Looking ahead, we plan to extend C# annotations beyond taint analysis to further enhance error detection capabilities.
Note. To learn more about C# user annotations, refer to the documentation.
The present and future of Unity
In 2024, the C# analyzer team focused on Unity-specific diagnostic rules.
Note. If you're interested in how static analysis can help you find bugs and optimize Unity projects, we invite you to read this article.
Unity-specific diagnostic rules:
As part of our GameDev research, we always explore new Unity versions. If you're curious to know what's new in Unity 6, we invite you to explore our review article.
In 2025, we plan to add even more optimization-focused and Unity-specific diagnostic rules. If you have suggestions for rules that would benefit Unity developers, we'd love to hear from you—feel free to email us!
Other enhancements
.plog and .json formats in Visual Studio.Diagnostic rules (General Analysis)
Micro-optimizations
Over a year, the C# team wrote over 20 articles about analyzing various projects and exploring different features of C#. Here are the most popular ones:
We also have a new regular series, .NET Digest. We cover the most interesting news and events in the world of .NET! You can read the latest installment here.
Taint analysis
The December release brought a new mechanism to the Java analyzer, taint analysis! Now we can develop diagnostic rules for taint analysis. This marks a significant step in our evolution as a SAST solution.
Taint analysis is a technology that helps track the external data flow. If such data reaches key areas of the code, it can lead to various vulnerabilities.
The first diagnostic rule for taint analysis in the Java analyzer, V5309, can detect potential SQL injections.
If you'd like to go a little deeper into the theory of what taint analysis is and how such mechanisms are implemented, I recommend reading our article about it.
Setting analysis timeouts in IDEA
We've added the option to set a timeout for analysis in the IDEA plugin. Now, you can specify a maximum duration, after which the analysis will automatically stop.
And that's not all! The next release will bring a lot of changes and improvements to our IDEA plugin. Stay tuned for updates :)
Diagnostic rules (General Analysis)
In 2024, we posted articles detailing the process of creating diagnostic rules. Highly recommended reading:
We've highlighted many of the most significant new features added to the analyzer in 2024, but this is only a glimpse into the full scope of changes. You can find a full list of changes in the release history.
Want to stay informed about future updates? Subscribe to our release digest. We also offer you to take a peek at our event and article digests.
What enhancements would you like to see in PVS-Studio in 2025? Share your ideas with us in the comments!
Don't forget to update to the latest version of PVS-Studio, which will include all of these enhancements! You can always find the most current version here.
0