There's a myth that open-source software is better and safer that the closed one. This was reasonably questioned many times. People regularly find epic vulnerabilities in the open source code. These vulnerabilities have been there for a long time. I think the project quality depends on how the development managers arrange the process and what methodologies/tools are used. It has nothing to do with the project being open source or closed source.
However, this myth is still alive. People believe that thousand eyes can inspect the code, and someone will find an error. I think you've got the idea.
As a PVS-Studio developer who found thousands of bugs in open-source projects, I am very sceptical about that. First, I doubt that someone is actually looking for errors and vulnerabilities. Second, being just this person, I can say that often developers don't care about these efforts. They may not be interested in the project's quality and reliability. They are interested in new features or something else, not the potential problems and security defects.
Authors of open-source projects ignored or put on the top shelf many of my bug reports. Do you want proof? Here. Today I have a perfect example.
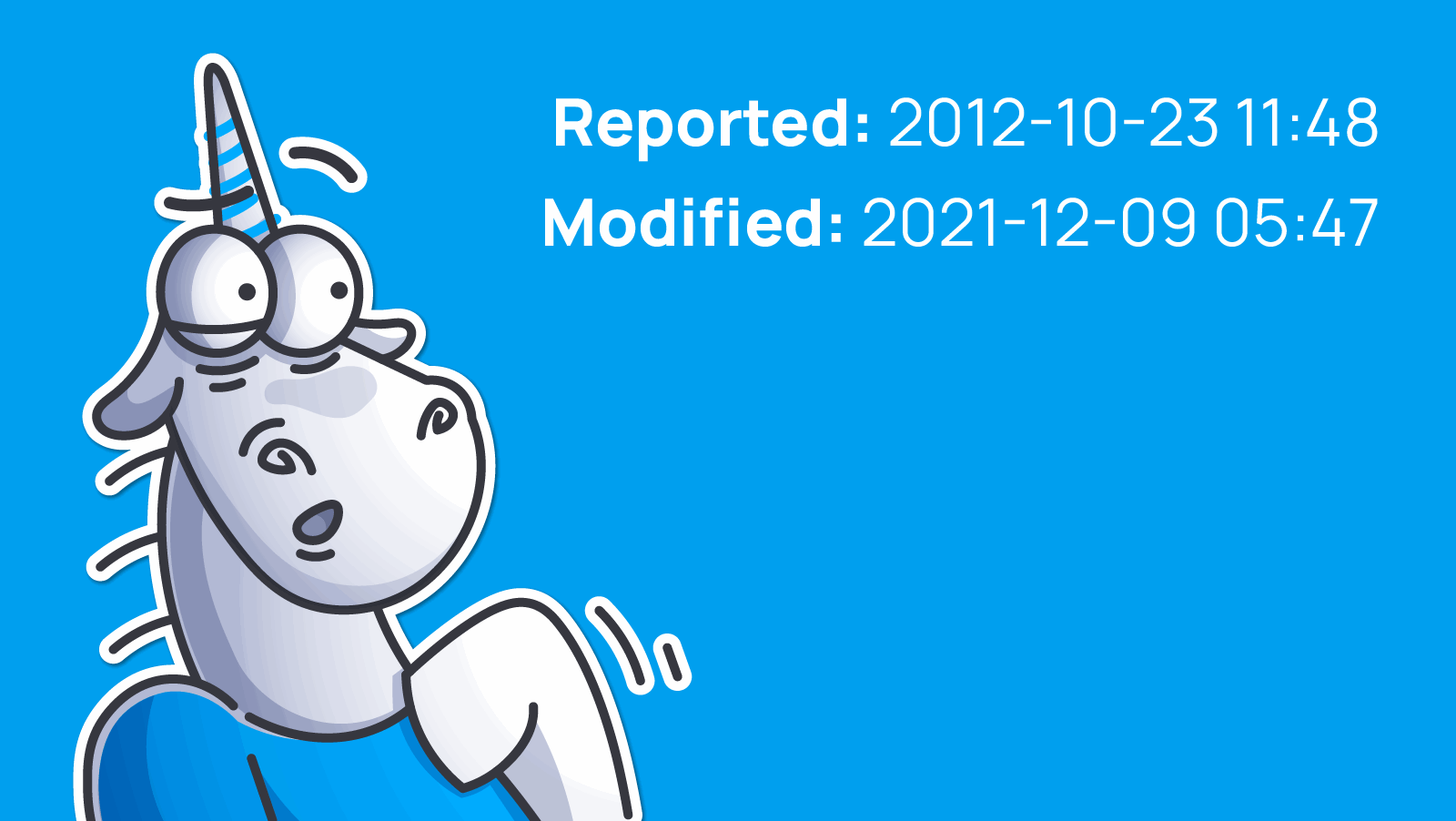
I was prompted to write this mini note by an unexpected message from the Samba project bugtracker. At first I didn't understand what kind of message it was. It turns out the developers got to bug report I left 9 years ago!

For nine years they ignored bugs in their project. For nine years they ignored the fact that their project has old versions of libraries with potential vulnerabilities like CWE-14. Even now (while I'm writing this note) the code has dangerous memset calls. Here, for example:
static void
md_result(MD_CTX * ctx, unsigned char *dst)
{
SHA256_CTX tmp;
memcpy(&tmp, ctx, sizeof(*ctx));
SHA256_Final(dst, &tmp);
memset(&tmp, 0, sizeof(tmp));
}Or here:
static void
calc(struct md2 *m, const void *v)
{
unsigned char x[48], L;
const unsigned char *p = v;
int i, j, t;
....
memcpy(m->state, x, 16);
memset(x, 0, sizeof(x));
}The compiler deletes these memset calls, and the private data will remain in memory. If you want to dive into this topic, you can read "Safe clearing of private data".
Maybe these bugs and security defects do not pose any real threat. But we're talking about another thing. The project developers don't care. Third-party developers don't care either. No one wants to search for and fix the bugs although static analyzers like PVS-Studio easily find them. No one wants to fix the bugs reported in bug reports.
I blew off the steam. I'm feeling better. Thanks for reading it :). Now I can refer to this note when someone says that open-source code is safer.
0