Flipper Zero is a pocket "multi-tool" for geeks, a treasure for pentesters, and your own cyber pet. All you need to take full advantage of Flipper Zero is your imagination and a set of certain skills.
In this article, we chat with the Flipper Zero developers. We invite fans of the device to delve into the history of its creation and explore its technical capabilities. If you are hearing about Flipper for the first time, you can learn more about it. Flipper has gone through bans, negativity, and praise. The project has brought together hundreds of thousands of enthusiastic hackers and people who are curious to learn more about the world around them. Have fun reading the article!
We talked to three developers — Alexander, Ivan, and Sergey. Energetic and positive, the team gathered to share with us one of the most important endeavors of their lives — the Flipper Zero project.
We'll discuss the following:
Alexander: Flipper Zero is a Tamagotchi for hackers. Or rather, a geek's Swiss Army knife that has evolved from a hacker's Tamagotchi to a full-fledged prototyping, development, and pentesting platform. In three years of the device existence, our team and community have written many different applications and tools in addition to the basic pentest functionality. They range from games and simple sensor interrogation programs to in-circuit debuggers. It's come to the point where Flipper can debug another Flipper, your Arduino, Raspberry Pi, or anything that has a debugging interface. And that's pretty cool.
First drafts and ideas were born during the development of access control and management systems. As is usually the case with hardware, the analysis and debugging tools are either not user-friendly or simply do not exist. Around the same time, we came up with the idea that it would be nice to have all this in one device with a user-friendly interface.

Picture 1. Source: Pikabu
These ideas and drafts turned into concepts, which turned into early prototypes and a Kickstarter campaign. After its success, the history of Flipper Devices Inn began.
Flipper Zero is not just a handy and compact gadget, it's your cyber friend. A dolphin was not chosen by chance. It's a reference to "Johnny Mnemonic" by the father of the cyberpunk subgenre, William Gibson. Even when you're not using the device, the little animal has a life of its own. You can play with it or feed it with some keys or cards. The latter is an original idea. Your Flipper is a hungry pet that embodies the hunger of curiosity. It gives hints and encourages the gadget owner to explore the world of technology.
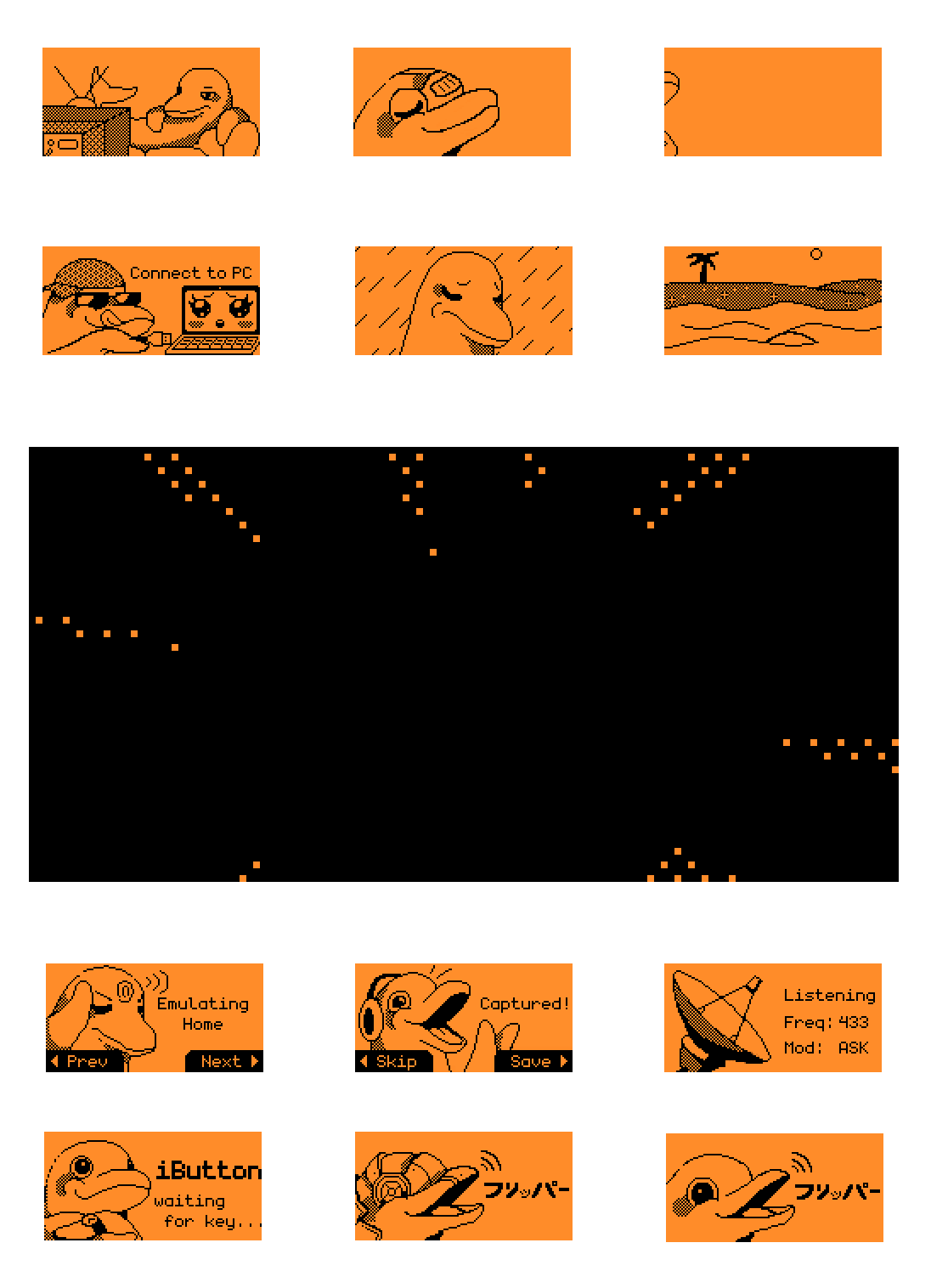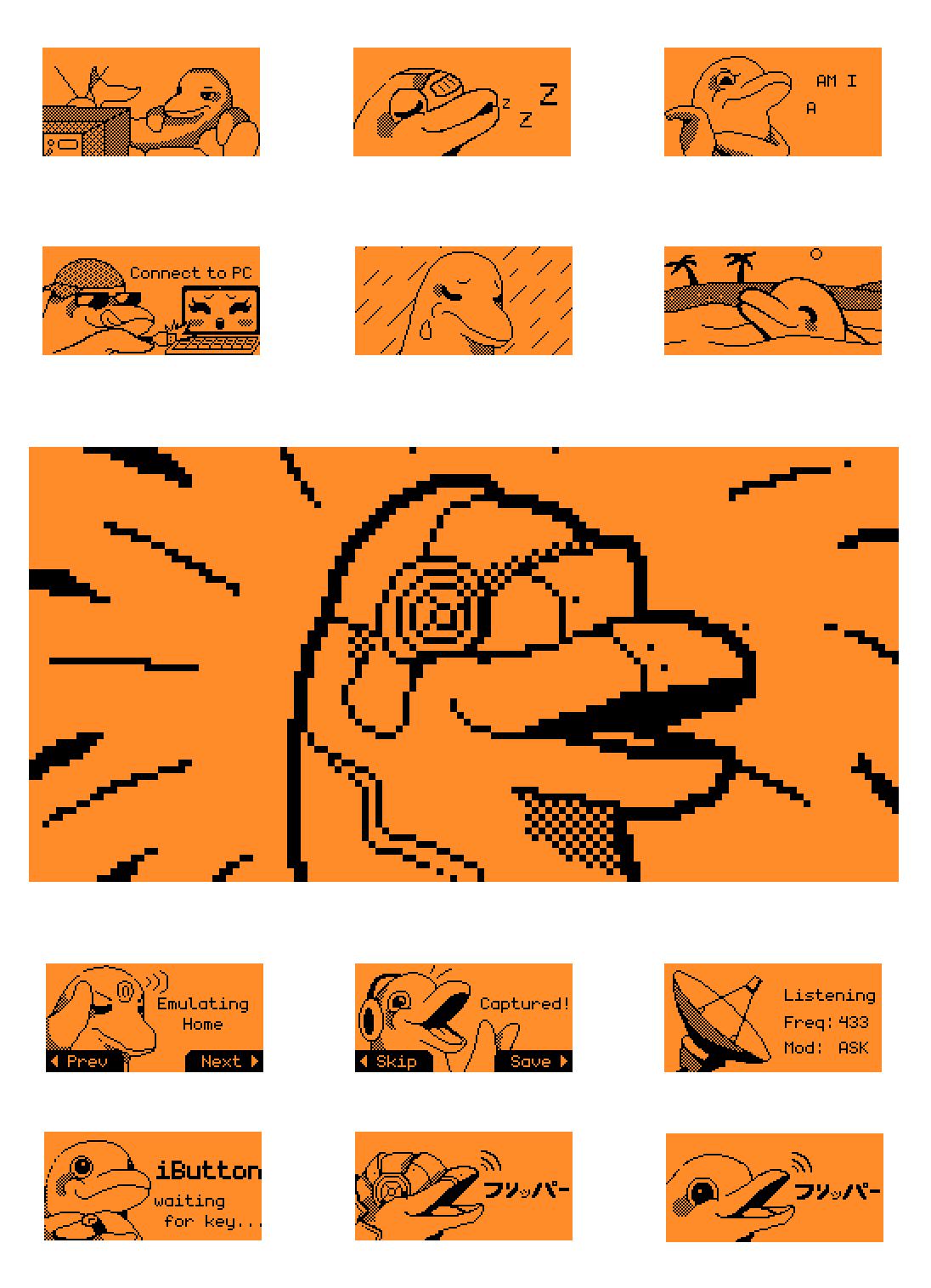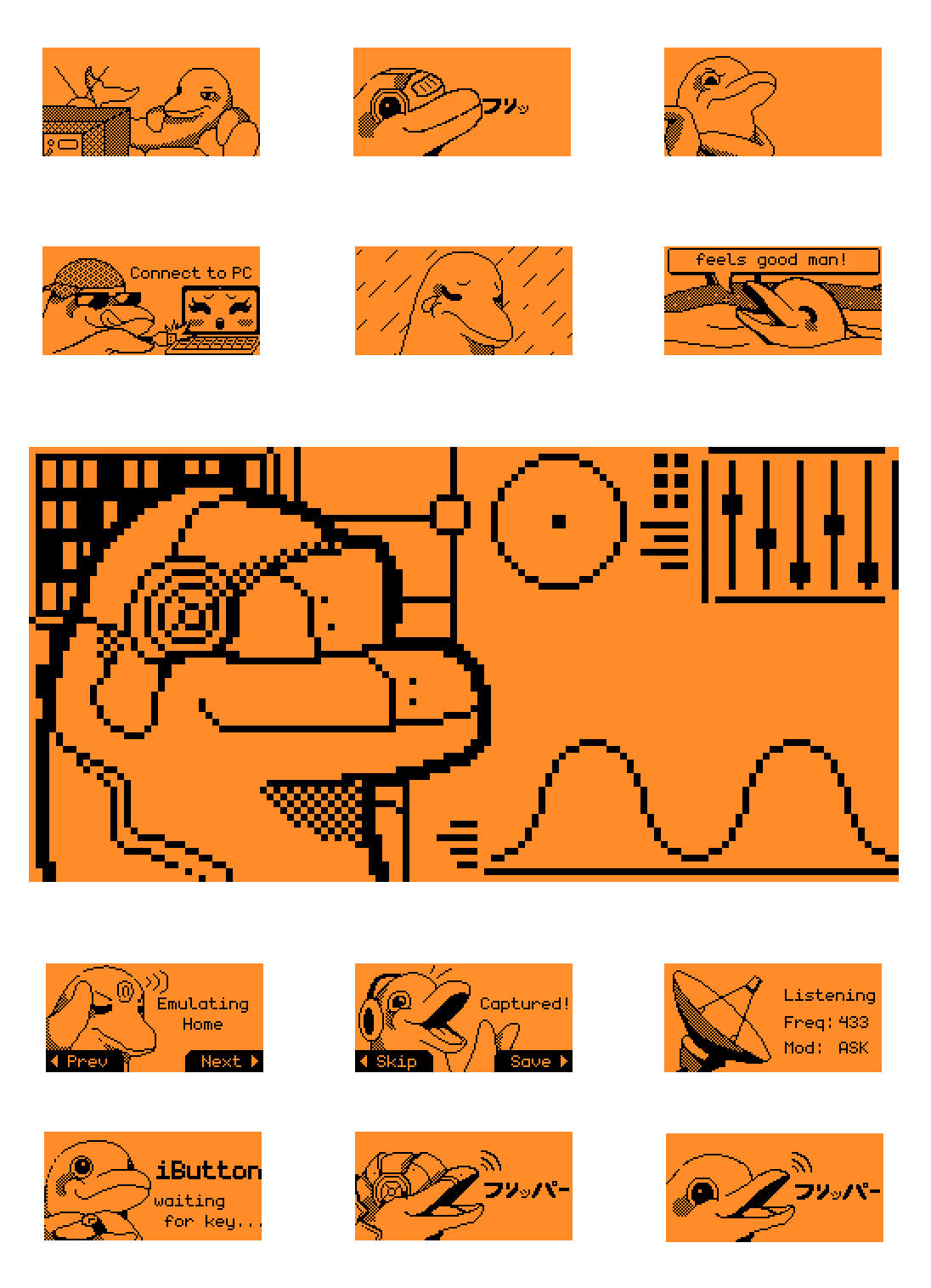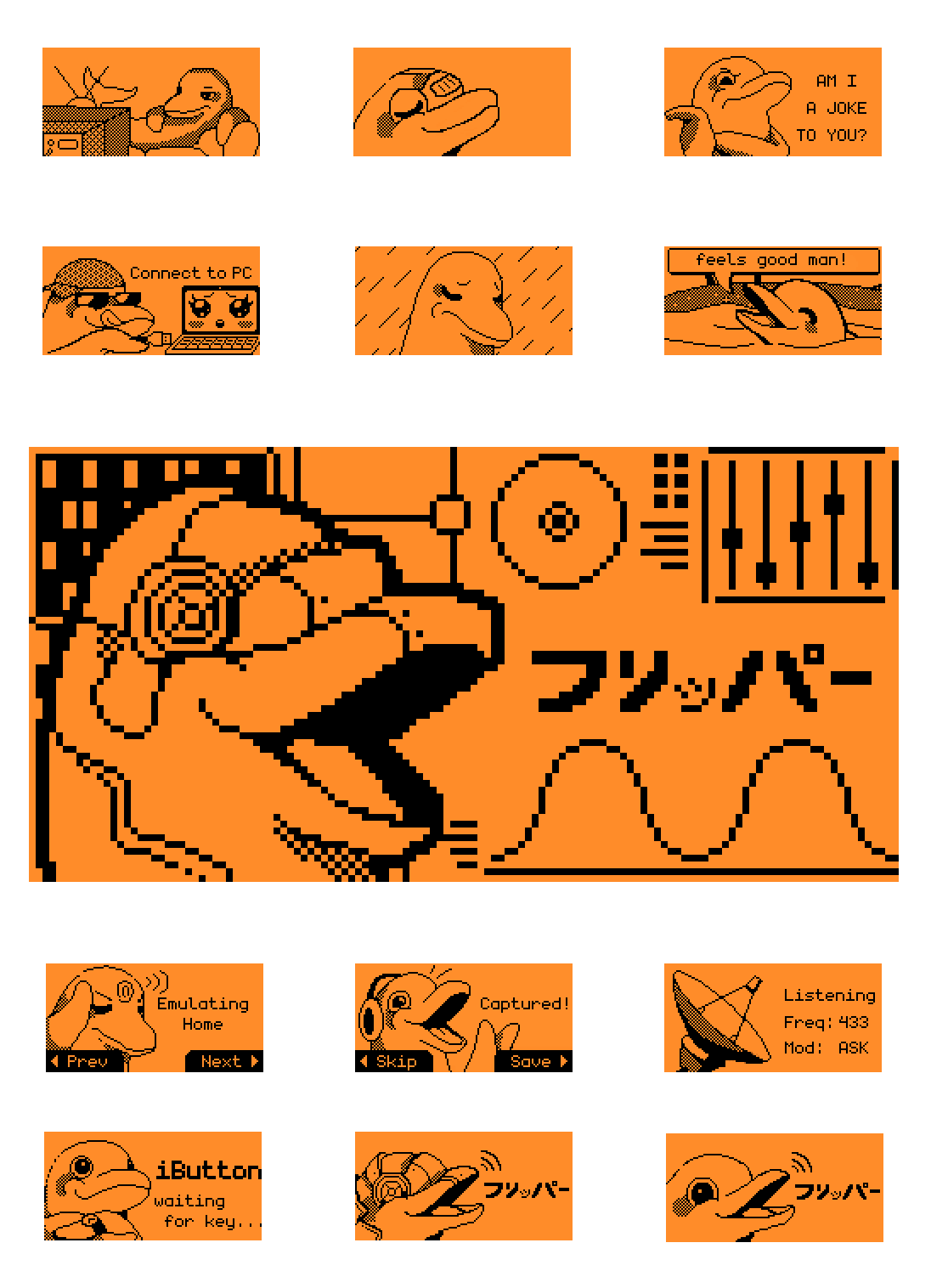
Upon unpacking, we see the phrase "Hack the planet", which is probably a reference to another project — pwnagotchi. Its developers, for their part, borrowed a phrase from Ian Softley's famous movie — "Hackers". By the way, pwnagotchi used to eat WPA handshakes and WiFi network PMKIDs.
Picture 4. Pwnagochi. Source: Pikabu
The way the device looks and its amber display are reminiscent of old Siemens phones. The idea wasn't just to "get nostalgic" about it. The point is that the display is perfectly visible in bright sunlight. It also has a very low power consumption — around 800 uA with the backlight off.
Flipper games are a different kind of nostalgia. Users have created many games of various complexity levels. There is text-to-speech chess, and you can also find simpler things like Tetris or Tic-tac-toe. There's a rock-paper-scissors game that you can play with another Flipper owner over the radio channel. There's a Doom analog and much more.
Overall, in terms of design and appearance, the devs have made a nice and user-friendly device.
The idea behind the device is to bring together all the hardware tools needed to research and develop on the go. Flipper turns your projects into a game and reminds you that development should always be fun.
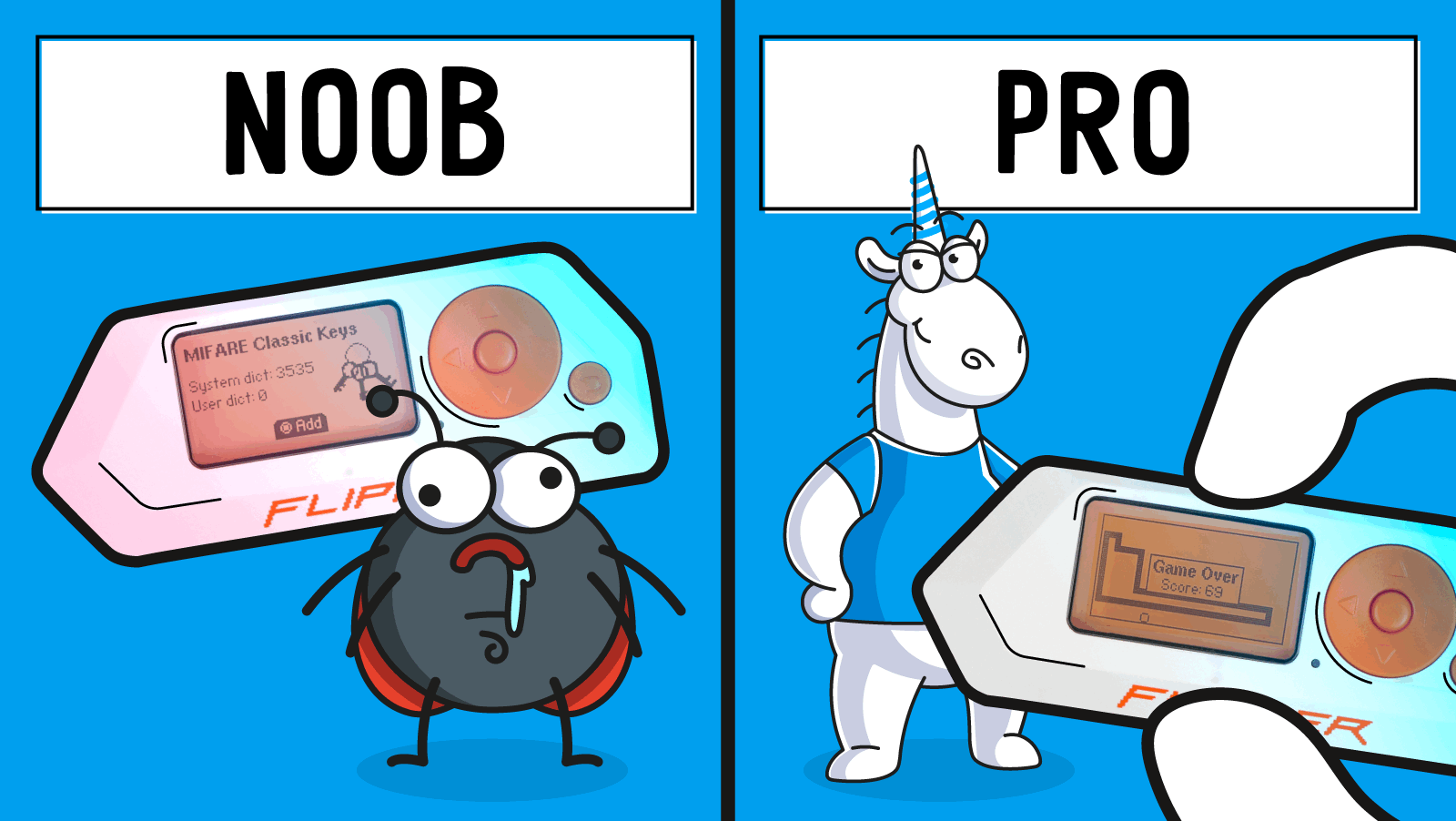
Alexander: Many people find it easy to use Flipper Zero right out of the box. The UI/UX is designed not to intimidate those who don't know anything. You have three functions for each subsystem: read, write, emulate. You can just poke around and explore the world. For example, you have a tag, and you're trying to figure out what it is. You bring up your device, you read it, and voila — you have an answer.
Of course, the world around us is a little bit more complicated than that. And if we talk about mifare, for example, it has unusual things like authentication. There are sectors with protected passwords. You need to know how to get the passwords by attacking the reader or the card. Everything about the basic functionality of our applications is described in the documentation. There are also guides on how to work with certain types of cards, for example. In addition, we have a fairly large community that develops different things. There are additional applications that greatly expand the functionality of the device. However, using them requires advanced knowledge.
Sergey: In addition to the basic functionality described in the documentation, we have a catalog of over a hundred applications. Of course, we can't monitor everything. The quality there is slightly different from the quality of our applications, including the documentation. That is, some things are not written at all.
Sergey: We can classify our users into 3 categories. Flip kiddie — people who bought Flipper because they saw Tesla sunroofs being hacked on TikTok; they saw how to turn off TVs in the store, and they wanted to do the same thing without deep understanding of it.

The second category is people who use Flipper all the time. They know how to use it to log into their computer, they write scripts for BadUSB. These people are interested in the world around them. For example, they see that there is an intercom. They look at what technology is used there: NFC, RFID, or iButton. They find the card, scan it with Flipper, explore the technology, and read about it. To unlock the potential of Flipper, you need to be interested in the world around you.
The third category is the superhumans who write applications for Flipper. A person from our community works in the cash registers service center. To not take his laptop with him, he wrote an application for Flipper that automates cash register maintenance.
Alexander: There is a more telling example for the second category: one of our first users is a paramedic. His job requires him to travel to various hospitals, so he has a stack of access cards. He copied them and now just walks around with Flipper, so he doesn't have to carry the cards around.
Sub-Ghz
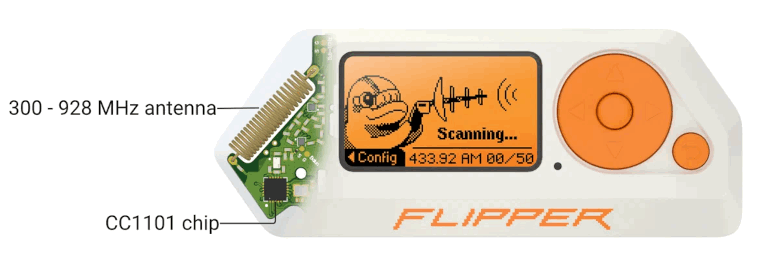
The integrated radio module is based on the TI CC1101 chip. It supports transmission and reception of digital signals in the frequency range of 300-928 MHz. This is the operating range for a wide class of access control devices and systems such as garage door openers, auto barrier gates, IoT sensors, and remote keyless entry systems. The RF transceiver is integrated with the modem, supports multiple modulation formats, and has a configurable data rate of up to 600 kbps.
125 kHz RFID

On the bottom of the Flipper case is an antenna that operates at 125 kHz. It can read LF RFID cards (EM-4100, HID, Indala, and so on), store them in memory, and emulate any of the stored cards by menu selection.
iButton
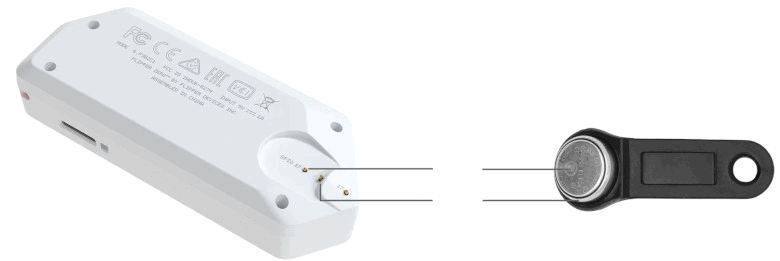
Flipper Zero supports a variety of button keys. The most popular are iButtons, which use the 1-wire protocol. When you attach the key, its protocol name appears on the screen above the ID number. In key emulation mode, the device acts as a key and emulates the iButton from the memory.
U2F
Flipper Zero can be used as the U2F token to work with services that support the protocol, such as Google, Twitter, Facebook, Dropbox, LastPass, Amazon AWS, and many others;
Alexander: U2F is actually a previous generation of protocols. It has now been replaced by FIDO. We'll add support for it later, too. Both protocols allow user authentication without the usual usernames and passwords. The idea is that you have a device, it has a set of private and public keys, and there's some kind of service that you want to authenticate with. When you register with the service, it connects with your U2F token, sends a registration request, and retrieves your public key. In addition, your U2F token has a record of registration with this service. And the next time you authenticate with the service, it will ask you for the U2F token to sign the request with a private key, verifying that you are who you say you are. This allows you to authenticate without logins and passwords.
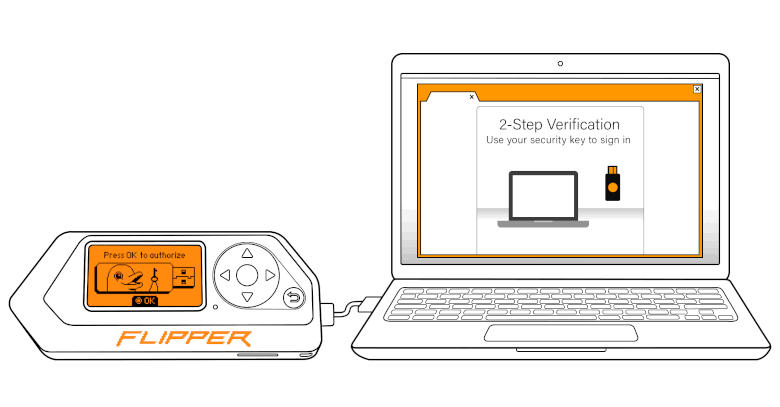
Note, however, that Flipper is not meant to replace hardware tokens, which have a crypto enclave and are specifically designed to store keys securely. We have the key encrypted with the unique key of the device, but if you try hard enough and access the device when it's unlocked, you can get the key.
Infrared
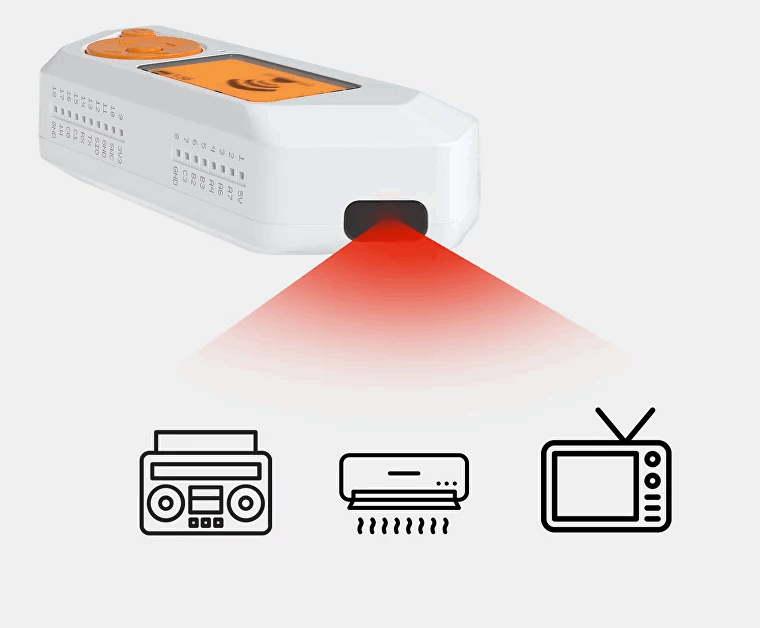
An infrared transmitter can send any signal to control electronics such as TVs, air conditioners, stereo systems, etc. The infrared module consists of an IR receiver based on TSOP75338TT, which allows to capture any IR signals with a carrier frequency of 38 kHz, and three VSMY14940 infrared emitting LEDs that operate at 940 nm.
Open-source code
Anyone can enhance the functionality of Flipper Zero by modifying the firmware code and/or writing custom applications.
SDK for all platforms
It is possible to develop apps for the device on all major platforms (Windows, macOS, Linux). For a quick start, there is the ufbt tool. With a single command, it enables you to install everything you need to start developing your application.
BadUSB
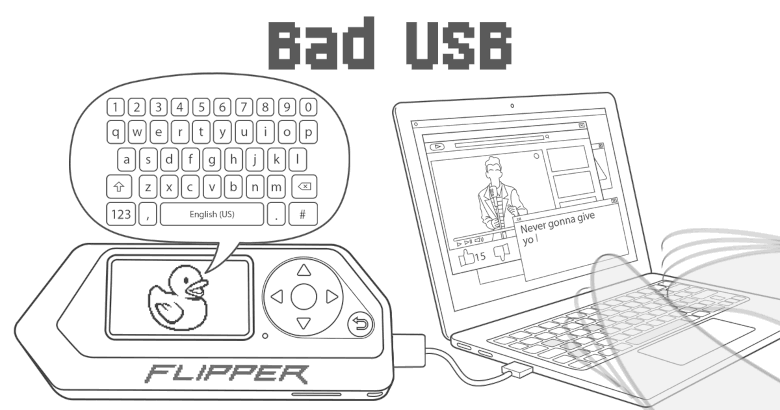
Flipper Zero can emulate input devices such as a keyboard or mouse and makes it possible to execute user-written scripts. This is how you can automate routine actions.
Bluetooth
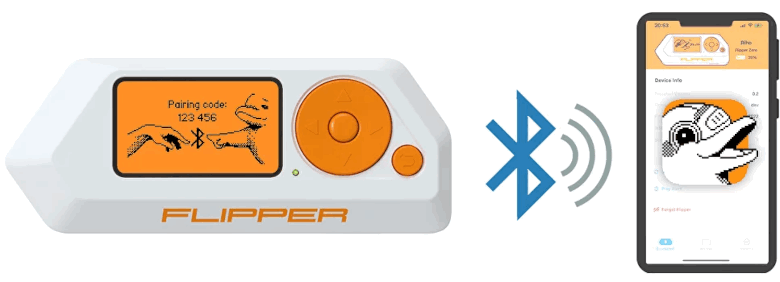
Flipper Zero has a built-in Bluetooth Low Energy module. As with the other wireless features of Flipper, an open-source library is available to add Flipper support to applications built by the community. With full BLE support, Flipper Zero can be used as a peripheral device.
The NFC module
The NFC module is based on the ST25R3916 controller. It's a high-performance universal NFC controller from STMicroelectronics that supports NFC initiator, NFC target, NFC reader, and NFC card emulation modes when required. Fully compatible with EMVCo 3.0 analog and digital devices, this NFC chip is optimized for POS terminal applications and provides the fastest possible interaction, even in harsh environments where the antenna is close to noisy LCD displays.
Flipper Zero can read certain frequencies, listen to radio channels, pick electronic locks, control household appliances, open gates, and much more. Flipper can read and emulate NFC tags, radio signals, and capture remote control signals via the built-in IrDA. It's a versatile tool for hardware exploration, firmware flashing, debugging, and fuzzing. You can connect it to any hardware device using GPIO to control it with buttons, run your own code, and display debug messages on LCD. You can also use it as a standard USB to UART/SPI/I2C/etc adapter.
Why do Flipper developers use Flipper?
Alexander: I use Flipper every day, for example, in development process. I often need a debugger when prototyping, so I use Flipper. I carry it with me all the time to turn off the TV, emulate different cards — Flipper has all this in one device and can also connect various external modules. It combines many different little things that can come in handy. It has a router, you can connect to its UART.
Sergey: Actually, in addition to Flipper being a universal keychain for everything, I had a case. I once rented a hotel room. There was no remote control for the air conditioner, which was set to a low temperature setting. With Flipper, I was able to control the air conditioner and make the temperature warmer. Also, since I design electronics, I often need to prototype something. For example, I just got a new display, and I need to run it to see what it looks like. I find it much easier and faster to prototype using Flipper than Arduino. Mainly because of the iteration speed. It's much faster to run code on Flipper than to flash some ESP32, STM32, or the same Arduino. As Alexander said, Flipper is a replacement for a very large number of devices: it's a pocket-sized USB to UART adapter, a CMSIS-DAP debugger, Atmega firmware, SPI flash firmware, a signal generator, and even a power supply. It even has an oscilloscope in user applications. It's a little weak, but Flipper has it.
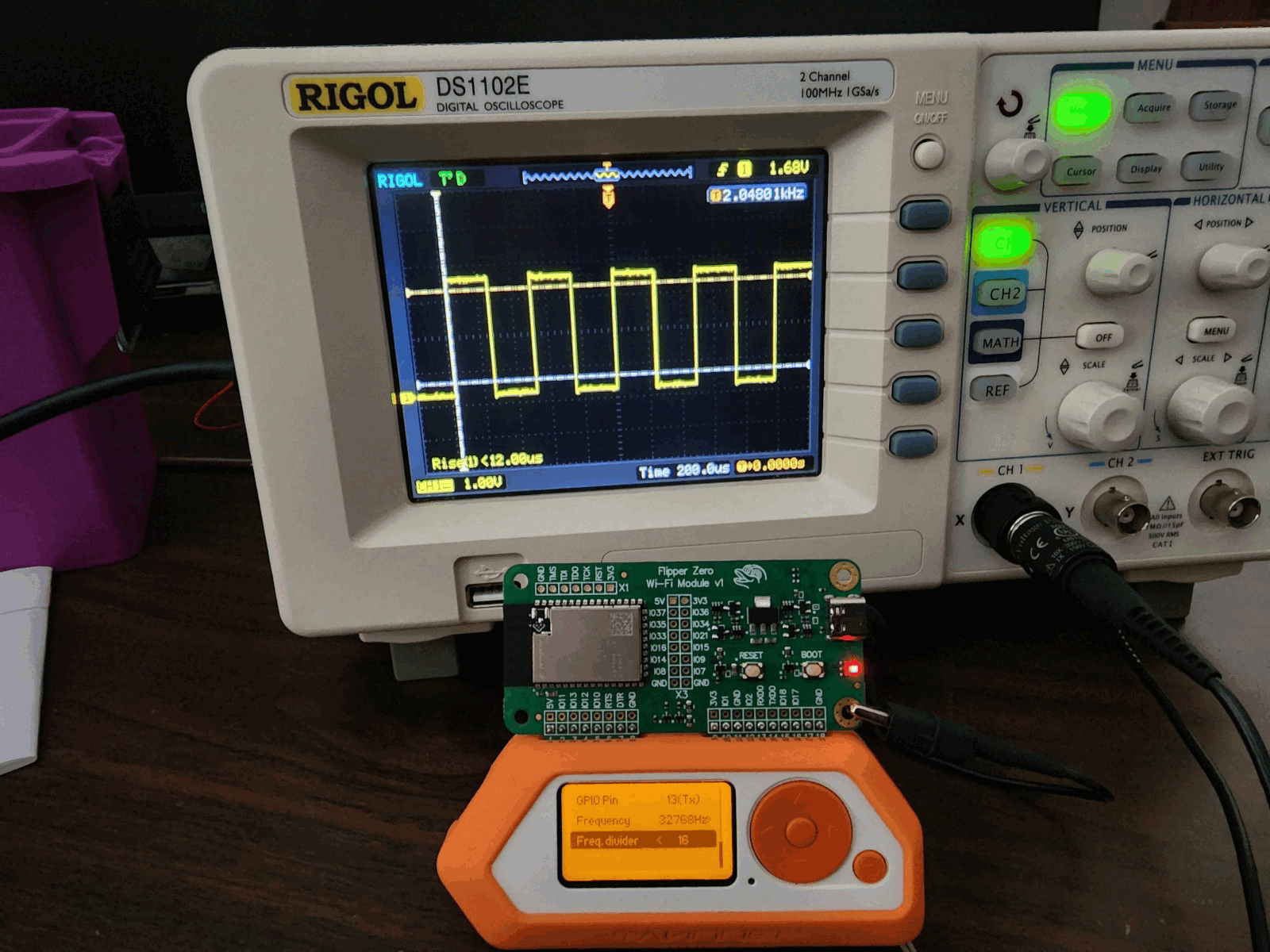
Picture 18. A Flipper user connected an oscilloscope to their Flipper. Source: reddit.com
Ivan: The big advantage is a significant number of pre-installed bases for infrared remotes for all kinds of systems, including TVs and air conditioners. It's really convenient. Sometimes you can't tune up the air conditioning system in the room you're in.
From the beginning, the project was an "explosion" on the Kickstarter crowdfunding platform. In just 8 minutes, the project raised 13 times more funds it originally needed to start production. Now, instead of the $60k planned, the platform has raised about $4.8 million.
You have a lot of fans overseas, a subreddit with 90k Flipper fans. Linus Sebastian (the Linus Tech Tips channel) posted a video review of the device some months ago. According to Sebastian, Flipper Zero is actually one of the most versatile hacking tools ever to hit the market. How do you feel when you hear something like that? What was the best praise you received made you feel proud?
Alexander: I feel that two and a half years of working 24/7 has not been in vain.
Sergey: I am happy when users say that the device does much more than they expected. It's also great to hear stories from users who have found their lost pets with the help of Flipper.
Ivan: A veterinarian can do the same thing, they have devices to read animal microchips. However, Flipper is always in your pocket. It might work a little worse, but it's always with you.
Alexander: Sometimes you can't just pick up a cat off the street and take it with you. If it has a passport, it should have a microchip. If an animal is lost, the microchip number can be used to quickly locate the animal and return it to its owner.
Picture 20. Source: docs.flipper.net
Ivan: The disadvantage of this system is that the microchip only stores its number and not the owner's contact information. There is no universal database for these microchip numbers worldwide. There are several independent databases in different countries that store the owner's contact information in the microchip number: the pet's name, the owner's phone number, possibly an address, and so on. Again, this is not a one-size-fits-all database. If you find such an animal and read the ID, you may have to check two or three databases before you find the owner. But overall, the system is good.
Sergey: I have an interesting story that involves these microchips. There is an advanced version with a thermometer. It is typically used on large animals. The farmer can simply walk through the herd with the reader to make sure none of the animals are sick. So, our co-worker had a microchip implanted in her shoulder, and now she can take her temperature using Flipper.
There is a downside of such success: problems in supplying the international market and government bans on importing the device in some countries. What are the concerns, and can Flipper Zero really be used for criminal purposes?
Alexander: For the three main destinations — Japan, Europe, and the USA — we immediately licensed the device and got all the necessary paperwork for import. There was just one problem: when a large shipment of devices comes into the country for the first time, customs sometimes has questions and requires additional papers. We happened to have a large container piling up for the States. That raised questions. It's true that Brazil banned Flipper from being imported.
The main problem here is that regulators often have no idea what they are regulating, and what the device can do. But they also watch TikTok and apparently think that everything there is true. Flipper isn't as evil as HackRF, for example, which is capable of much scarier things. At some point, something triggered customs regulators, and they decided that we couldn't import Flipper into Brazil. Somewhere along the line, it seemed like we delivered the message that our tool could do no harm out of the box. So far, however, we have not made any progress.

There was one more thing. At the very beginning, we added support for reading bank card information. Reading bank card information is not an unusual process. In fact, you read the same number that is on your card. Sometimes, when you use Apple Pay on your iPhone, for example, you'll read only the virtual card number. This information is simply impossible to use. Unfortunately, any mention of card reading really triggers the regulators.
Sergey: Technically, your phone can also read this information from bank cards.
Ivan: Nothing that doesn't require physical access to the card is happening. There isn't enough information to use it with malicious intent. Still, the mere presence of this feature raised questions.
Sergey: There was an article in the US where a policeman stated that Flipper Zero was a carjacking device. There was a lot of hype around it. This is simply because this device is promoted as a hacking multi-tool. But we do not mean "hacking" as in bank robbery or carjacking. First of all, a hacker is a person who tries to understand how things work around them. The next day after the article was published, the same publication issued a retraction. They said that Flipper Zero is not that bad, everything is good and clean. However, it left an unpleasant aftertaste. Most problems are caused by misunderstandings and misconceptions about the role of the device.
Alexander: There's a lot of technically complex stuff inside the device, and when you start digging into it, you understand where the line between legal and illegal is drawn. It's not clear to most people who don't deal with these systems. All the more reason not to expect regulators to understand it. There is nothing wrong with that, there have been similar situations with most of the regulators in different countries. You just go to them, explain, show them the documents, and the questions disappear.
Ivan: In Brazil, it all comes down to the fact that they told us to bring the device for certification. We applied for certification for an import permit. They didn't issue the import permit. But "you can try to certify it", sure. There have been some absurd situations like this.
Alexander: Wherever we publish anything, we always preach the principles of ethical hacking. If it isn't yours, don't go there. If you're going to break something, you should at least get permission. Many users who are professionally auditing secure-embedded systems, — for whom this device was created in the first place, — use it absolutely legally from the white hats' point of view, they get all the permissions.
Anything you do with something that doesn't belong to you is at least a gray area. Then it depends on the laws. For example, in some states, it's a crime to simply cross the border through the opening auto barrier gates.
The device initially covers short-range protocols. It implies that if you have physical access to that card, then, apparently, it's your card.
Of course, theoretically, it could be used to do harm. It's like wielding a knife. You can use a knife to make dinner, or you can use a knife to do some damage.
Ivan: We had legality and barrier gates in mind. There are two main types of access. The first is static, where the keychain always sends the same code. The second is dynamic codes, when a new package is generated each time. Once the barrier has got a package from a legitimate key fob, it will not accept the same package again. This is a so-called primitive defense against repeated attacks. It is based on what has already been captured in the air. The standard Flipper firmware is designed to accept a wide range of signals, both static and dynamic. However, the stock firmware only allows the transmission of received static signals. Otherwise, transmitting someone else's dynamic code will cause their key fob to become unsynchronized. This means that the person whose fob is actually legitimate (and we can't verify whose signal we're actually intercepting) will have to press the button a few times before the barrier opens. To avoid such situations, we do not transmit dynamic signals in the stock firmware.
Sergey: In this case, you can even exaggerate and say that if a legitimate owner of a key fob with dynamic code copies it with Flipper, and then sends the copied signal to Flipper, they can get the original key fob that doesn't work.
Ivan: So, we don't allow it to avoid such situations. However, Flipper implements many of these protocols at the transmission level. We can create a new key fob of this format and bind it to the security system. Flipper will be able to work with a security system that supports dynamic codes. However, it won't be a copy of the key fob. It will behave like a legitimate new key fob of the same format.
When we were choosing which protocols to support, we broke them down into different groups:
All devices in this group have to balance between "how evil is it?" and "what values are we trying to convey, what exactly are we trying to do with this device?" If we talk about Flipper, we're trying to make the device give you a sense of what the world around you is like and how safe it is. But at the same time, we eliminate any dangerous activities that feel illegal. This applies to almost all car protocols. A large number of them are insecure, such as the central locking systems in cars. We don't add them as a matter of principle. Simply because the damage done by such actions would be much greater than we expected.
Alexander: Negative reviews happen to everything for different reasons. I haven't seen any really negative ones. Often the negativity comes from users who don't fully understand what the device is all about. There are people who are against the very existence of such a device. They claim there should be no such gadgets since they always bring evil.
Sergey: I remember a negative review from a person. They believed that Flipper was a universal device that could opening every door and required no special knowledge on the user's part. Since we are the open-source project, users can develop their own firmware. So, they installed one of the "evilest" (I even put it in quotes to emphasize) firmware. It was written in a very messy way. As a result, in their review, the device was very unstable and crashed all the time.
Alexander: We do not consider it an "app store" as a matter of principle. We call it an "application catalog". There are a few reasons. Usually, "app stores" don't like it when someone gives competition and tries to sell something. But beyond that, we have a concept. We have an open-source device, and we want our applications to be open source, so that they can be enhanced. The idea of open source code. You can drop a link to code from your GitHub repository, it will all build up, and go into the catalog. Flipper has a basic operating system installed on the device, the rest is applications. Our major applications, such as NFC and RFID, are now also on the SD card. We have created quite many applications and a debugger. Users can install all of these apps that have been added to the app catalog via a phone or PC.
Sergey: When an application has open-source code, it is very difficult to control it, to verify that a person has purchased the application and not pirated or compiled it themselves. There are also many legal and technical complexities associated with apps selling. That's why we have a catalog, not a store. We have a great variety of applications and games in our catalog right now. There's an app, for example, that lets you check the weather and humidity by scanning the radio waves for weather station sensors.
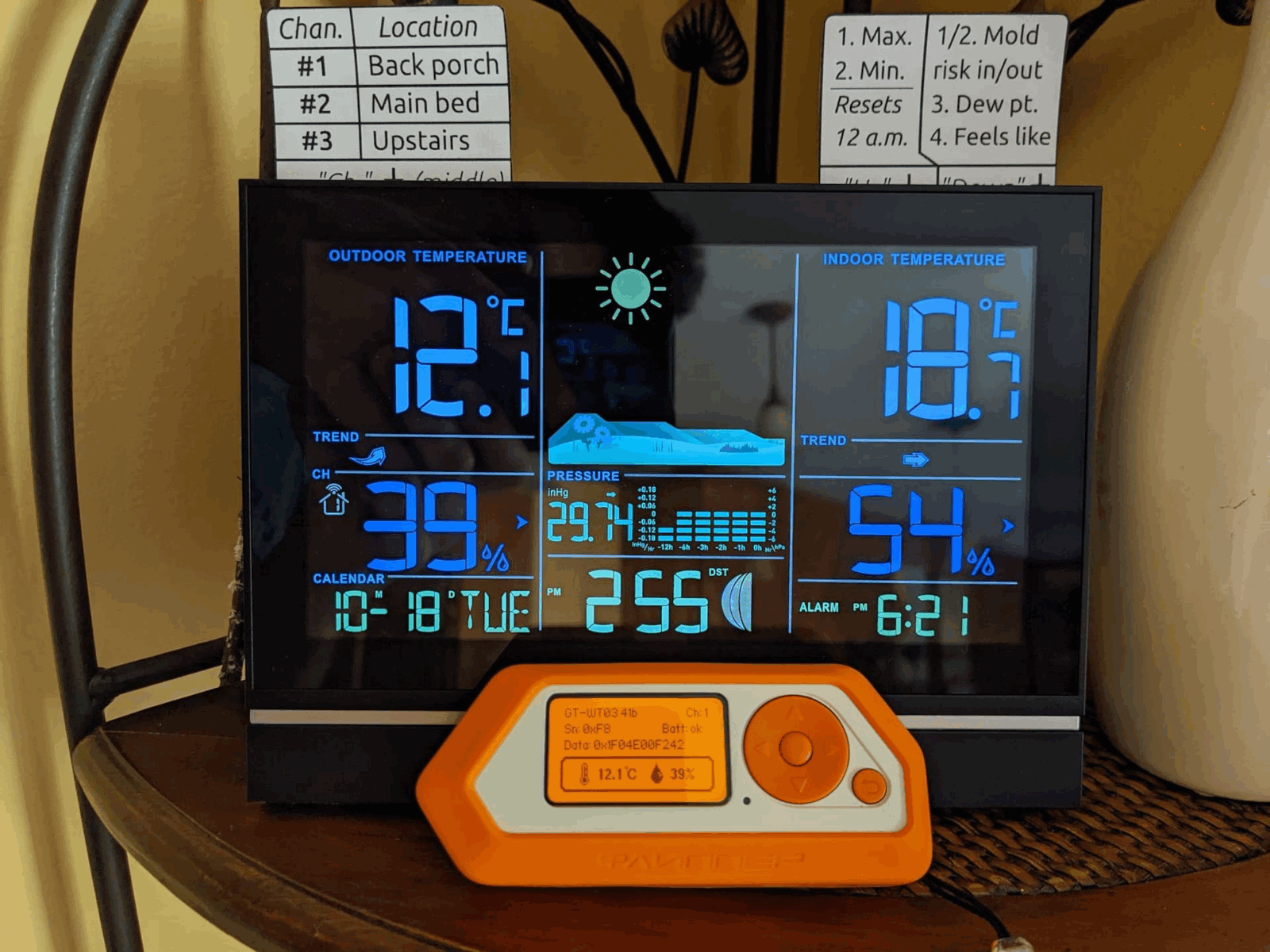
Picture 25. Source: forum.flipper.net
Ivan: So as not to be unfounded, here is a link to the catalog, you can view it in your browser. Here's an up-to-date list of what you can install on your mobile device in just two taps.
Sergey: Yes, to our surprise, we have many games in our catalog: Snake, Chess, Asteroids, Arkanoid, Sokoban, Flappy Bird, tic-tac-toe, a Doom analog, and even rock-paper-scissors with the radio channel multiplayer. I even saw a review from a user who complained that his girlfriend took Flipper from him and wouldn't give it back. She plays Tetris on it.
Alexander: Besides applications, we have external modules. The community develops not only applications but also modules for them, like the Geiger counter. For example, there are people who make external modules to work with cards. They create an additional authentication system for these cards. The scope of freedom is virtually limitless. We are now preparing a new generation of modules. There will be CAN-BUS, CAN-LIN, RS-232, RS-485, Air Mouse, gyroscope, accelerometer, compass, barometer, and one interesting Raspberry project.
Sergey: HID-USB and HID-BLE are among the most popular applications in the catalog. With them, Flipper can act as a wired/wireless keyboard and mouse. I use it as a remote for music, a remote for my smartphone camera, a presentation remote clicker, a remote scene switcher, and occasionally, when I don't have a keyboard, I use Flipper to configure a server. Flipper can also emulate other USB devices, such as hard drives. 12 megabits per second (USB 2.0 Full Speed) is pretty sad. It will take days to install a modern operating system from such a hard drive. But it is perfectly capable of emulating floppy disk images or bootable disks, for example.
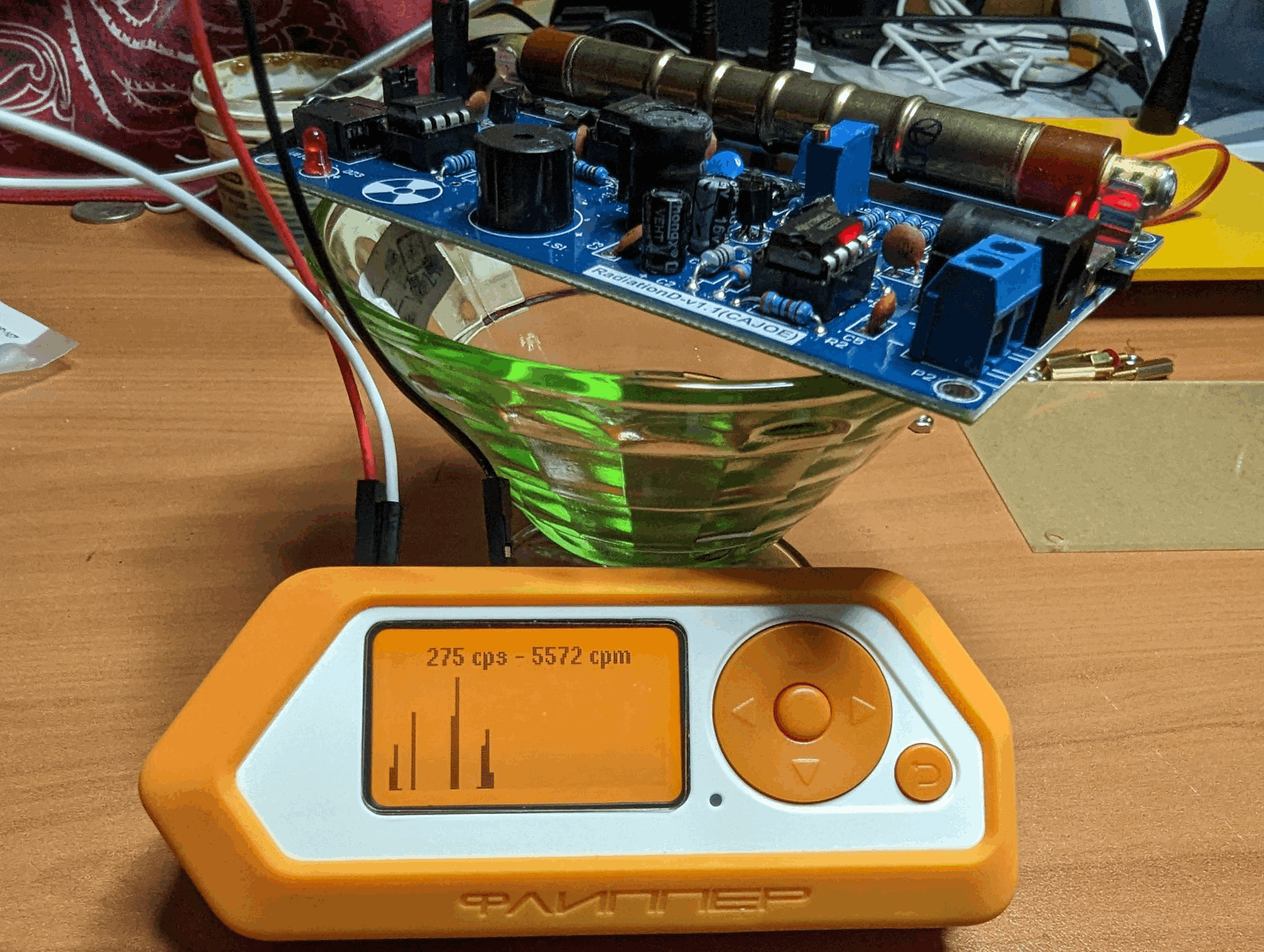
Picture 26. Photo of a user who has installed a Geiger counter on Flipper. Source: reddit.com
Alexander: It became clear that we would be developing the next product. We want to present it next year, but we'll see how it goes. It will be better, faster, more powerful, and have more features. We realized that we all started with simple microcontrollers in one way or another. Some of us started with very old ones. The understanding of what a modern microcontroller is has dramatically changed. In the past, you would write a program, and you would have nothing but this little, simple program on your microcontroller. And the logic was quite simple, linear. But with Wi-Fi and whatnot coming out of the IoT world, it became clear that there was a need for a full-fledged operating system. Some processes and services have already appeared, they interact with each other. Unfortunately, not many microcontroller manufacturers consider this. There is Nordic, they develop their Zephyr based system.
Picture 27. Zephyr
It is an open-source RTOS supported by the Linux Foundation. Unfortunately, Zephyr is quite heavy. In our case, it was just not a good fit at the beginning of our project. We got something very similar and more compact. We came up with the idea of simplifying everything. This way, even newbie developers could use it. Our goal for hardware is clear: to release the next generation, more advanced, faster, and with a bigger screen. On the other hand, we know exactly what we want to do in terms of software. We want to give microcontroller developers a development-friendly operating system, not the usual stuff from the "embedded" world.
Ivan: Yes, we have opened an application catalog. But the foundation to get it going was laid late last year/early this year. We made it technically possible to run applications from an SD card on an embedded device without MMU and without virtual memory management. To my knowledge, this has never been seen before in mass-produced equipment. We have, in fact, the first device that offers user-friendly development environment and the capability to run a portable application. It can be ported between different firmware versions, even as compiled binary code. The API compatibility is also maintained. You can run the application on different firmware versions of your device. This is also quite an accomplishment. It provided an opportunity to push the development level on the community part to where it is now.
Sergey: We have also put a lot of effort into the build system that builds applications for the catalog. As a result, we have ufbt — a Python package that handles all the development stuff we need. In addition to compiling applications, it provides configurations for IDEs, tools for loading and running code on Flipper, a terminal emulator, and the option to fully debug applications in a convenient way, with breakpoints and other memory lookups.
Ivan: With native development, it's always a headache to deploy the development environment, i.e. to put in toolchains, libraries, to configure everything. We put it in separate packages for all major platforms: Windows, Linux, and macOS. We have written the build system to be quite minimalistic: when you start it, it automatically downloads everything without cluttering the user's path. It just neatly uses the toolchain it brought with it. This reduces the start of development to a few commands that deploy everything. They form the basis of an application that you can run on Flipper in 2 minutes.
The backstory. From time to time, our team checks open-source projects using the PVS-Studio static analyzer. Developers write articles in which they tell about interesting errors they have found in open-source projects. This is an opportunity for us to show what the tool is capable of and to entertain the developer community with interesting content.
In 2021, PVS-Studio co-founder and DevRel Andrey Karpov wrote an article about the checking of the Flipper Zero project. The Flipper team supported him, and we published our first collaborative article with the authors' comments on the errors found by the analyzer. Since then, the Flipper developers have been active users of our analyzer. Since the project has open-source code, the guys can use PVS-Studio for free. We are happy to contribute a small part to the project development. At the end of our conversation, the guys decided to share their experiences of working with the static code analyzer.

Ivan: PVS-Studio has been integrated into our toolset for almost a year now. The initial integration was a real headache. I think you know what it's like to remove all the warnings and rewrite everything in an existing project. We've had some big ones that have been really painful. We have designed malloc in such a way that it either returns something valid or causes the system to crash. This behavior had to be suppressed pretty much everywhere, a whole family of warnings, that's about 3 or 4. And then there's the C template library, and it's badly written. It caused a lot of warnings. Defines hide outrageous statements that sometimes have empty fields or strange structures. We've suppressed many warnings just in macros for this library.
A note from the PVS-Studio developers: For our users, we would like to point out that the issue regarding the special malloc function is no longer relevant. There is a special markup, it tells the analyzer to consider that the function always returns a non-null pointer:
//V_RET_NOT_NULL, function: [namespace::][class::]functionNameSee the "Additional configuration of C and C++ diagnostic rules" documentation section for this and other special features.
Sergey: It's actually very nice when people write, "I've been using your device for three months, and it's been very stable. I've only had to reboot it a couple of times". But our codebase is huge — hundreds of thousands of lines. It's not a full-fledged OS with MMU where we can handle an abnormal situation. It's an embedded system. If the system crashes, the only way to recover it is a reboot. To achieve such stable work, we use a lot of tools, strict compiler settings, asserts everywhere, automated QA, and, of course, the PVS-Studio analyzer.
Flipper Devices Inc is a team of creative and ambitious developers. Attention to detail and care for the users are key components of their success. The team captured the hacker's adventurous spirit and finesse in one small but clever box. And it's far from over.
Below this article, we've compiled a list of useful resources to help you better understand how Flipper works. We wish you all clean code and creative ideas!
Subscribe to our monthly digest, so you can have access to our best articles on code quality and others.
ZDNET: 7 cool and useful things to do with your Flipper Zero
The Verge: The Flipper Zero is a Swiss Army knife of antennas
IEEE Spectrum: The Flipper Zero: A Hacker's Delight
WIRED: Hands On With Flipper Zero, the Hacker Tool Blowing Up on TikTok
0