SCA (software composition analysis) with PVS-Studio
PVS-Studio not only searches for weaknesses in code, but also searches for vulnerable components used in an application. Why does the analyzer do that?
Danger in vulnerable components
Modern applications often use third-party components, some of which have security weaknesses. If an application uses a vulnerable component, it can also become vulnerable to malicious attacks. Therefore, companies risk their reputation and finances.
The OWASP Top 10 2021 has a separate category for using vulnerable and outdated components: A06:2021 – Vulnerable and Outdated Components.
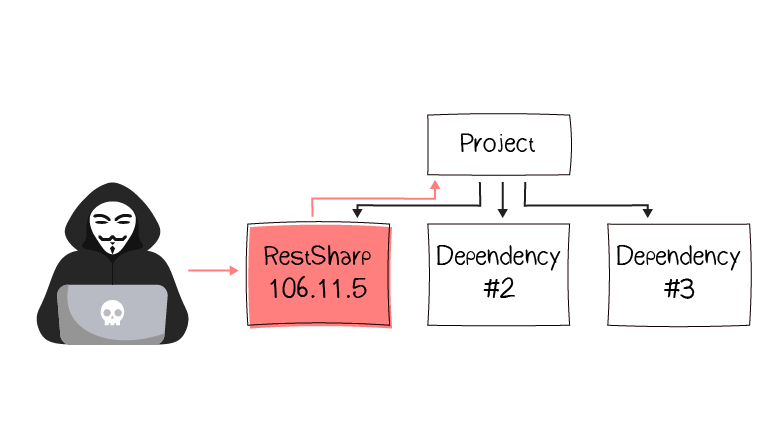
Is it possible to automatically check that the application doesn't use components with known vulnerabilities? Yes. To do this, specialized tools perform software composition analysis (SCA).
SCA tools inspect what components the application consists of. If they find vulnerable components, they notify the developers. After that the developers can update/replace the component, or protect the application in other ways.
PVS-Studio as SCA solution
As of now, PVS-Studio performs software composition analysis only in C# projects. Do you want to have the same feature for projects in C, C++, or Java? Let us know.
PVS-Studio analyzes a project and determines which components it uses. If the analyzer finds a vulnerable one — it issues a warning. This warning contains the name and version of a dangerous component, description of a vulnerability, and CVE-ID.
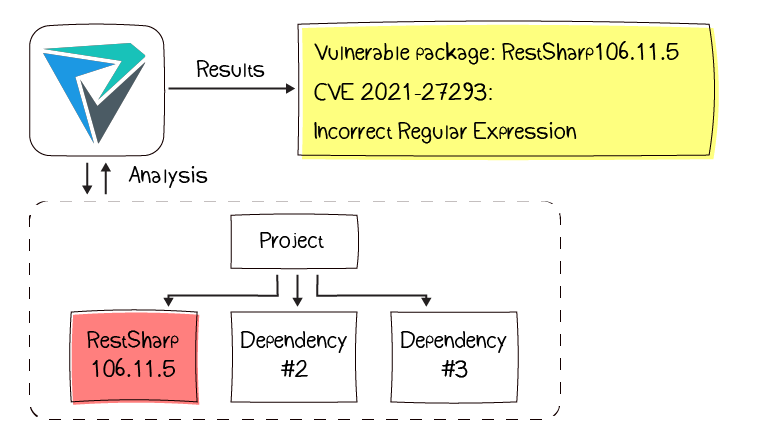
The V5625 diagnostic rule analyzes software components. The documentation describes how to work with the SCA warnings and fine-tune them for a specific project.
