DevOps is a methodology aiming at establishing closer collaboration between programmers and system administrators in the software development process. A DevOps engineer is a specialist working on the intersection of these two fields. A DevOps engineer's primary objective is to take the predictability, efficiency, and security of software development to the highest level possible. DevSecOps is a further development of the DevOps concept that, besides automation, addresses the issues of code quality and reliability assurance.

Let's talk about the DevOps methodology first. Its objective is to unite the activities related to development, quality assurance, deployment, and integration. DevOps can be called a philosophy that aims at building up a culture of collaboration between originally isolated teams. Software development and deployment operations have been traditionally carried out by two different persons or departments. DevOps aims at improving the efficiency by eliminating the boundaries between these two phases of software development. For any technical specialist, DevOps is a key factor in optimizing time and resources for better productivity, understanding, and training.
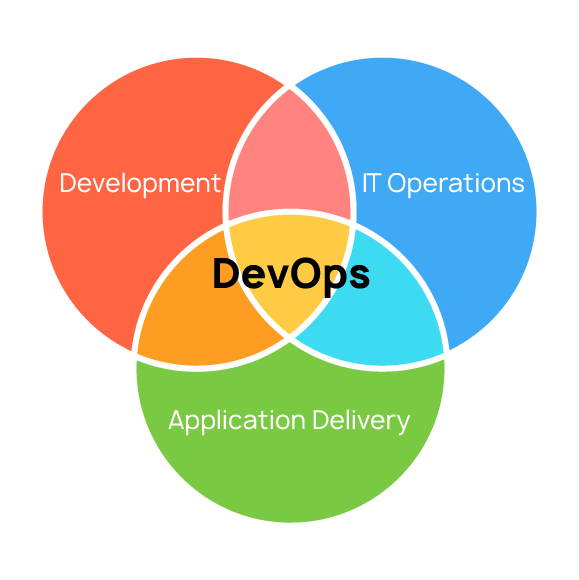
DevOps includes:
Since this job title emerged quite recently, at the end of the '00s, it has no precise definition yet. We suggest the following definition: a DevOps engineer is a person who helps an organization adopt the DevOps methodology.
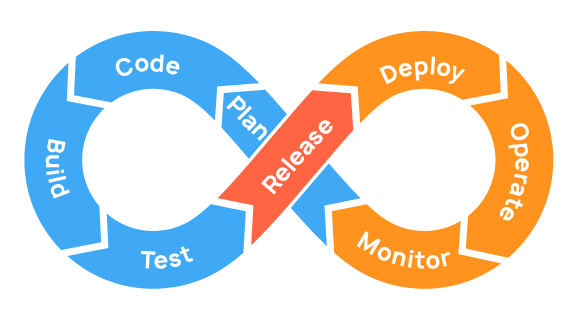
There is a set of areas that a DevOps engineer must be competent in:
Next, we'll answer the question asked at the very beginning of this post.
Similarly to DevOps, DevSecOps can also be called a culture of its own. DevSecOps is a philosophy of integrating security methods into a DevOps process. Team work is as crucial to a DevSecOps engineer as it is to a DevOps engineer: their ability to resolve conflicts and conduct productive negotiations plays a crucial role in creating secure applications. From the very start of a SDLC, DevSecOps works to make the application secure by introducing a variety of security techniques.
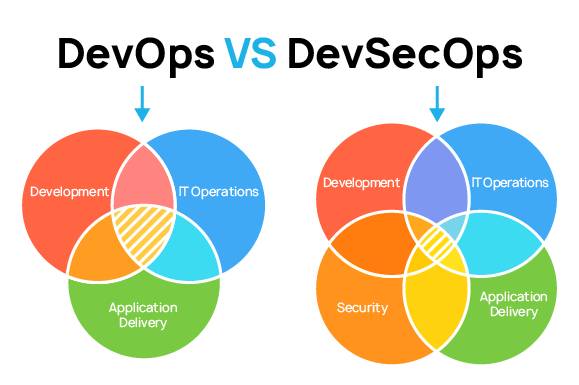
DevOps heavily relies on automation. The same is true for DevSecOps, which aims at automating every aspect, including security audit.
To stimulate the adoption of DevSecOps, the Cloud Security Alliance company has defined six fundamental aspects, or pillars:
The transition from DevOps to DevSecOps requires understanding the particular techniques and practices ensuring software security. Let's discuss this aspect in more detail and find out what technologies exactly will be needed.
First, I suggest adopting Dynamic Application Security Testing (DAST) tools. As tools performing the so called black-box testing, dynamic analyzers can identify program vulnerabilities such as SQL injections, buffer overflows, and the like. Building dynamic analyzers into your software development process is one of the steps towards the DevSecOps practices.
Runtime Application Self-Protection (RASP) is one of the security technologies used at runtime. RASP analyzes the application's behavior, thus implementing continuous security analysis.
Interactive Application Security Testing (IAST). The IAST approach analyzes the application from the inside at runtime and keeps track of code execution in memory, looking for specific events that could lead to a vulnerability. These events are further analyzed to see if they are clean or pose a risk of causing a vulnerability.
Static Application Security Testing (SAST) is used to check the code without actually executing it. SAST helps find potential vulnerabilities in the source code, thus preventing multiple possible zero-day vulnerabilities. Common Weakness Enumeration (CWE) is one of the most popular classifications of warnings produced by SAST tools. CWE is an official list or dictionary of common security weaknesses exploitable by intruders to obtain unauthorized access to the system. Using a static analyzer as part of the development process will help prevent software bugs from getting to the next level, CVE. CVE (Common Vulnerabilities and Exposures), is a database of widely known information security vulnerabilities, which was worked out as an attempt to make an ordered list of known software defects.
Software Composition Analysis, SCA. SCA can identify vulnerabilities in open-source components and analyze applications to see if they include components that are known to contain vulnerabilities. See also "The risks of using vulnerable dependencies in your project, and how SCA helps manage them".
Let's recap.
DevSecOps is a practice of integrating security objectives into the DevOps methodology. Security automation in DevOps is an aspect that requires new approaches, technologies, and tools. DevSecOps can be viewed as an extension of the DevOps methodology since DevSecOps builds on it. If you want to learn more on the topic, the following resources should be helpful:
0