PVS-Studio is a static application security testing tool (SAST). In other words, the PVS-Studio analyzer detects not only typos, dead code and other errors, but also potential vulnerabilities.

There are two approaches to detecting vulnerabilities in code.
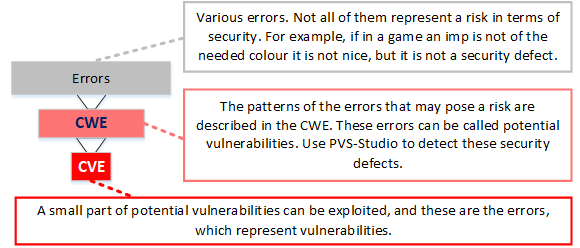
The first one implies that the analyzer searches dangerous fragments in code drawing on the base of common vulnerabilities CVE. It is similar to the work of antiviruses. This approach is effective for detecting known vulnerabilities, which could get in the project when using old libraries or due to the Copy-Paste method.
Nevertheless, this solution doesn't give the answer to the question what to do with newly written code and vulnerabilities that haven't been detected yet.
Therefore, there is the second approach when parts of code that contain security defects are preventively detected and fixed. This strategy is currently implemented in the PVS-Studio tool.
There is a Common Weakness Enumeration (CWE) base, which describes patterns of errors, which can be exploited as vulnerabilities under certain circumstances. Indeed, in practice, only a very small part of CWE-errors is dangerous. From a developer's point of view, it makes no sense to speculate whether a flaw can be used for an attack or not. You just need to fix all the defects, and thus improve the reliability of your application.
The PVS-Studio analyzer supports classification of errors according to CWE. If PVS-Studio issued a warning and matched that with one from CWE ID, it means that a potential vulnerability is detected and it has to be fixed.
I recommend checking out another article on a similar topic -"How Can PVS-Studio Help in the Detection of Vulnerabilities?". It describes some vulnerabilities, which can be found using PVS-Studio at the stage of code writing.
Introduce the PVS-Studio static code analyzer in your development process to enhance the quality and reliability of the projects you develop.
0